
What is the best CEH v12 exam solution?
It is CEH v12 books, online video tutorials, discussion groups…
But the best CEH v12 exam solution I shared today is EC-COUNCIL 312-50v12 dumps: https://www.leads4pass.com/312-50v12.html, candidates should know that passing practice and mock exams can help you make great progress and pass the exam with ease.
leads4pass 312-50v12 dumps contains 528 exam questions and answers, and provides two learning formats: 312-50v12 dumps pdf and 312-50v12 dumps VCE, providing you with the most friendly learning solution!
312-50v12 exam questions from part of CEH v12 Exam Solutions
—PS. Participate in the 312-50v12 online practice to learn more about CEH v12 Exam Solutions
| From | Number of exam questions | Exam name | Exam code |
| leads4pass | 15 | Certified Ethical Hacker Exam (CEHv12) | 312-50v12 |
Question 1:
Don, a student, came across a gaming app in a third-party app store and Installed it. Subsequently, all the legitimate apps on his smartphone were replaced by deceptive applications that appeared legitimate. He also received many advertisements on his smartphone after Installing the app.
What is the attack performed on Don in the above scenario?
A. SMS phishing attack
B. SIM card attack
C. Agent Smith’s attack
D. Clickjacking
Correct Answer: C
Agent Smith Attack Agent Smith attacks are carried out by luring victims into downloading and installing malicious apps designed and published by attackers in the form of games, photo editors, or other attractive tools from third-party app stores such as 9Apps.
Once the user has installed the app, the core malicious code inside the application infects or replaces the legitimate apps in the victim\’s mobile device CandC commands.
The deceptive application replaces legitimate apps such as WhatsApp, SHAREit, and MX Player with similar infected versions.
The application sometimes also appears to be an authentic Google product such as Google Updater or Themes. The attacker then produces a massive volume of irrelevant and fraudulent advertisements on the victim\’s device through the infected app for financial gain.
Attackers exploit these apps to steal critical information such as personal information, credentials, and bank details, from the victim\’s mobile device through CandC commands.
Question 2:
Which tool can be used to silently copy files from USB devices?
A. USB Grabber
B. USB Snoopy
C. USB Sniffer
D. Use Dumper
Correct Answer: D
Question 3:
Juliet, a security researcher in an organization, was tasked with checking for the authenticity of images to be used in the organization\’s magazines. She used these images as a search query and tracked the original source and details of the images, which included photographs, profile pictures, and memes. Which of the following footprinting techniques did Rachel use to finish her task?
A. Reverse image search
B. Meta search engines
C. Advanced image search
D. Google advanced search
Correct Answer: C
Question 4:
Bob, your senior colleague, has sent you a mail regarding a deal with one of the clients. You are requested to accept the offer and you oblige. After 2 days, Bab denies that he had ever sent a mail. What do you want to “know” to prove to yourself that it was Bob who had sent a mail?
A. Non-Repudiation
B. Integrity
C. Authentication
D. Confidentiality
Correct Answer: A
Non-repudiation is the assurance that someone cannot deny the validity of something. Non-repudiation is a legal concept that is widely used in information security and refers to a service, which provides proof of the origin of data and the integrity of the data. In other words, non-repudiation makes it very difficult to successfully deny who/where a message came from as well as the authenticity and integrity of that message.
Question 5:
Which of the following tools are used for enumeration? (Choose three.)
A. SolarWinds
B. USER2SID
C. Cheops
D. SID2USER
E. DumpSec
Correct Answer: BDE
Question 6:
Take a look at the following attack on a Web Server using obstructed URL:
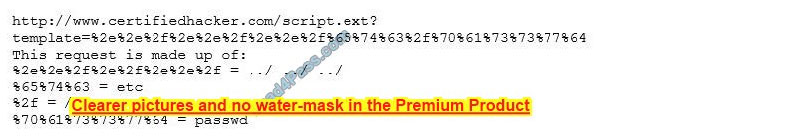
How would you protect yourself from these attacks?
A. Configure the Web Server to deny requests involving “hex encoded” characters
B. Create rules in IDS to alert on strange Unicode requests
C. Use SSL authentication on Web Servers
D. Enable Active Scripts Detection at the firewall and routers
Correct Answer: B
Question 7:
A DDOS attack is performed at layer 7 to take down web infrastructure. Partial HTTP requests are sent to the web infrastructure or applications. Upon receiving a partial request, the target servers open multiple connections and keep waiting for the requests to complete.
Which attack is being described here?
A. Desynchronization
B. Slowloris attack
C. Session splicing
D. Phlashing
Correct Answer: B
Developed by Robert “RSnake” Hansen, Slowloris is DDoS attack software that permits one computer to require down an internet server.
Due to the straightforward yet elegant nature of this attack, it requires minimal bandwidth to implement and affects the target server\’s web server only, with almost no side effects on other services and ports.
Slowloris has proven highly effective against many popular sorts of web server software, including Apache 1. x and 2. x. Over the years, Slowloris has been credited with a variety of high-profile server takedowns.
Notably, it had been used extensively by Iranian `hackivists\’ following the 2009 Iranian presidential election to attack Iranian government internet sites. Slowloris works by opening multiple connections to the targeted web server and keeping them open as long as possible.
It does this by continuously sending partial HTTP requests, none of which are ever completed. The attacked servers open more and connections open, expecting each of the attack requests to be completed. Periodically, the Slowloris sends subsequent HTTP headers for every request, but never actually completes the request.
Ultimately, the targeted server\’s maximum concurrent connection pool is filled, and extra (legitimate) connection attempts are denied. By sending partial, as against malformed, packets, Slowloris can easily elapse traditional Intrusion Detection systems. Named after a kind of slow-moving Asian primate, Slowloris really does win the race by moving slowly and steadily.
A Slowloris attack must await sockets to be released by legitimate requests before consuming them one by one. For a high-volume internet site, this will take a while. the method is often further slowed if legitimate sessions are reinitiated.
But in the end, if the attack is unmitigated, Slowloris–like the tortoise–wins the race.If undetected or unmitigated, Slowloris attacks also can last for long periods of your time. When attacked sockets outing, Slowloris simply reinitiates the connections, continuing to reach the online server until mitigated.
Designed for stealth also as efficacy, Slowloris is often modified to send different host headers within the event that a virtual host is targeted, and logs are stored separately for every virtual host.
More importantly, within the course of an attack, Slowloris is often set to suppress log file creation. this suggests the attack can catch unmonitored servers off-guard, with no red flags appearing in log file entries.
Methods of mitigationImperva\’s security services are enabled by reverse proxy technology, used for inspection of all incoming requests on their thanks to the clients\’ servers.Imperva\’s secured proxy won’t forward any partial connection requests–rendering all Slowloris DDoS attack attempts completely and utterly useless.
Question 8:
Nicolas just found a vulnerability on a public-facing system that is considered a zero-day vulnerability. He sent an email to the owner of the public system describing the problem and how the owner can protect themselves from that vulnerability. He also sent an email to Microsoft informing them of the problem that their systems are exposed to. What type of hacker is Nicolas?
A. Red hat
B. white hat
C. Black hat
D. Gray hat
Correct Answer: B
A white hat (or a white hat hacker) is an ethical computer hacker, or a computer security expert, who focuses on penetration testing and other testing methodologies that ensures the safety of an organization\’s information systems.
Ethical hacking may be a term meant to imply a broader category than simply penetration testing.
Contrasted with the black hat, a malicious hacker, the name comes from Western films, where heroic and antagonistic cowboys might traditionally wear a white and a black hat respectively.
While a white hat hacker hacks with good intentions with permission, and a black hat hacker, most frequently unauthorized, has malicious intent, there\’s a 3rd kind referred to as a gray hat hacker who hacks with good intentions but sometimes without permission.
White hat hackers can also add teams called “sneakers and/or hacker clubs”, red teams, or tiger teams.
While penetration testing concentrates on attacking software and computer systems from the beginning? scanning ports, examining known defects in protocols and applications running on the system, and patch installations, as an example? ethical hacking may include other things.
A full-blown ethical hack might include emailing staff to invite password details, searching through executives \’s dustbins, and typically breaking and entering, without the knowledge and consent of the targets. Only the owners, CEOs, and Board Members (stakeholders) who asked for such a censoring of this magnitude are aware. to undertake to duplicate a number of the destructive techniques a true attack might employ, ethical hackers may arrange for cloned test systems, or organize a hack late in the dark while systems are less critical.
In most up-to-date cases these hacks perpetuate for the long-term con (days, if not weeks, of long-term human infiltration into an organization).
Some examples include leaving USB/flash key drives with hidden auto-start software in a public area as if someone lost the tiny drive and an unsuspecting employee found it and took it.
Some other methods of completing these include:?
DoS attacks?
Social engineering tactics?
Reverse engineering?
Network security?
Disk and memory forensics?
Vulnerability research?Security scanners such as:?
W3af?
Nessus?
Burp suite?
Frameworks such as:?
Metasploit?
Training PlatformsThese methods identify and exploit known security vulnerabilities and plan to evade security to realize entry into secured areas. they\’re ready to do that by hiding software and system `back-doors\’ which will be used as a link to information or access that a non-ethical hacker, also referred to as `black-hat\’ or `grey-hat\’, might want to succeed in.
Question 9:
Which of the following types of SQL injection attacks extends the results returned by the original query, enabling attackers to run two or more statements if they have the same structure as the original one?
A. Error-based injection
B. Boolean-based blind SQL injection
C. Blind SQL injection
D. Union SQL injection
Correct Answer: D
Question 10:
Bob is doing a password assessment for one of his clients. Bob suspects that security policies are not in place. He also suspects that weak passwords are probably the norm throughout the company he is evaluating. Bob is familiar with password weaknesses and key loggers.
Which of the following options best represents the means that Bob can adopt to retrieve passwords from his client’s hosts and servers?
A. Hardware, Software, and Sniffing.
B. Hardware and Software Keyloggers.
C. Passwords are always best obtained using Hardware key loggers.
D. Software only, they are the most effective.
Correct Answer: A
Question 11:
Kevin, an encryption specialist, implemented a technique that enhances the security of keys used for encryption and authentication. Using this technique, Kevin input an initial key to an algorithm that generated an enhanced key that is resistant to brute-force attacks.
What is the technique employed by Kevin to improve the security of encryption keys?
A. Key derivation function
B. Key reinstallation
C. A Public key infrastructure
D. Key stretching
Correct Answer: D
Question 12:
Every company needs a formal written document that spells out to employees precisely what they are allowed to use the company\’s systems for, what is prohibited, and what will happen to them if they break the rules.
Two printed copies of the policy should be given to every employee as soon as possible after they join the organization. The employee should be asked to sign one copy, which should be safely filed by the company. No one should be allowed to use the company\’s computer systems until they have signed the policy in acceptance of its terms.
What is this document called?
A. Information Audit Policy (IAP)
B. Information Security Policy (ISP)
C. Penetration Testing Policy (PTP)
D. Company Compliance Policy (CCP)
Correct Answer: B
Question 13:
Tony is a penetration tester tasked with performing a penetration test. After gaining initial access to a target system, he finds a list of hashed passwords.
Which of the following tools would not be useful for cracking hashed passwords?
A. John the Ripper
B. Hashcat
C. netcat
D. THC-Hydra
Correct Answer: A
Question 14:
Abel, a cloud architect, uses container technology to deploy applications/software including all its dependencies, such as libraries and configuration files, binaries, and other resources that run independently from other processes in the cloud environment.
For the containerization of applications, he follows the five-tier container technology architecture. Currently. Abel is verifying and validating image contents, signing images, and sending them to the registries.
Which of the following tiers of container technology architecture Is Abel currently working in?
A. Tier-1: Developer machines
B. Tier-4: Orchestrators
C. Tier-3: Registries
D. Tier-2: Testing and accreditation systems
Correct Answer: D
The official management decision is given by a senior agency official to authorize the operation of an information system and to explicitly accept the risk to agency operations (including mission, functions, image, or reputation), agency assets, or individuals, based on the implementation of an agreed-upon set of security controls. formal declaration by a designated accrediting authority (DAA) or principal accrediting authority (PAA) that an information system is approved to operate at an acceptable level of risk, based on the implementation of an approved set of technical, managerial, and procedural safeguards. See authorization to operate (ATO).
Rationale: The Risk Management Framework uses a new term to refer to this concept, and it is called authorization.
Identifies the information resources covered by an accreditation decision, as distinguished from separately accredited information resources that are interconnected or with which information is exchanged via messaging.
Synonymous with Security Perimeter. For the purposes of identifying the Protection Level for the confidentiality of a system to be accredited, the system has a conceptual boundary that extends to all intended users of the system, both directly and indirectly connected, who receive output from the system.
See authorization boundary.
Rationale: The Risk Management Framework uses a new term to refer to the concept of accreditation, and it is called authorization. Extrapolating, the accreditation boundary would then be referred to as the authorization boundary.
Question 15:
Attacker Rony Installed a rogue access point within an organization\’s perimeter and attempted to Intrude into its internal network. Johnson, a security auditor, identified some unusual traffic in the internal network that is aimed at cracking the authentication mechanism.
He immediately turned off the targeted network and tested for any weak and outdated security mechanisms that are open to attack.
What is the type of vulnerability assessment performed by Johnson in the above scenario?
A. Distributed assessment
B. Wireless network assessment
C. Most-based assessment
D. Application assessment
Correct Answer: B
Expanding your network capabilities is often done well using wireless networks, but it also can be a source of harm to your data system.
Deficiencies in its implementations or configurations can allow the tip to be accessed in an unauthorized manner.
This makes it imperative to closely monitor your wireless network while also conducting periodic Wireless Network assessments.
It identifies flaws and provides an unadulterated view of exactly how vulnerable your systems are to malicious and unauthorized access.
Identifying misconfigurations and inconsistencies in wireless implementations and rogue access points can improve your security posture and achieve compliance with regulatory frameworks.
…
And that’s just a part, get 528 latest 312-50v12 exam questions and answers: https://www.leads4pass.com/312-50v12.html (312-50v12 dumps)
Your future:

Various companies across different industries may require or prefer employees with CEH v12 certification, particularly in roles related to cybersecurity, ethical hacking, penetration testing, and network security. Some of the types of organizations that often seek individuals with CEH v12 certification include:
IT Consulting Firms: Companies that provide cybersecurity consulting services often value CEH v12 certification. These firms offer expertise and support to other organizations in securing their networks, conducting vulnerability assessments, and ensuring overall cybersecurity.
Government Agencies: Government entities, such as defense and intelligence agencies, may require CEH v12 certification for personnel involved in cybersecurity operations, incident response, or penetration testing. These organizations deal with sensitive information and require skilled professionals to protect their systems and networks.
Financial Institutions: Banks, insurance companies, and other financial organizations are prime targets for cyberattacks. They typically need cybersecurity professionals with CEH v12 certification to identify vulnerabilities and protect against potential threats.
Technology Companies: Organizations specializing in software development, network infrastructure, cloud services, and other technology sectors often seek employees with CEH v12 certification. These companies prioritize strong cybersecurity practices to safeguard their products, services, and customer data.
Healthcare Providers: The healthcare industry handles sensitive patient information and medical records, making it a prime target for cybercriminals. Healthcare organizations often prioritize CEH v12 certification for their cybersecurity teams to help protect patient data and ensure compliance with industry regulations.
E-commerce and Retail: Online retailers and e-commerce platforms rely on secure transactions and customer data protection. They may require CEH v12 certification to strengthen their cybersecurity posture and defend against threats like payment fraud, data breaches, and website defacement.
Defense Contractors: Companies working in defense and military sectors often require CEH v12 certification for their personnel involved in cybersecurity and ethical hacking activities. These organizations need to protect critical infrastructure and sensitive data from cyber threats.
It’s important to note that the need for CEH v12 certification can vary between organizations, and it ultimately depends on their specific cybersecurity requirements and industry regulations. It’s advisable to review job postings, company policies, and industry trends to identify organizations that value the CEH v12 certification in their hiring and promotion processes.
You can also see everything else about Certified Ethical Hacker (CEH) v12: https://thecyberexpress.com/everything-we-know-about-certified-ethical-hacker-v12/
Salary:
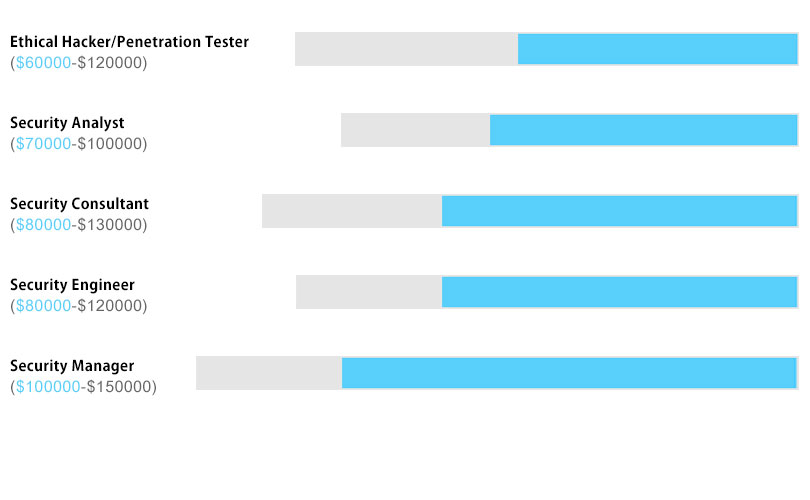
The salary you can expect with a CEH v12 certification will depend on several factors, including your experience, location, job role, industry, and the specific organization you work for. While I can’t provide precise salary figures, I can give you a general idea of the salary range for professionals with CEH v12 certification.
In general, the CEH v12 certification is considered a valuable credential in the field of cybersecurity and ethical hacking, which can positively impact your earning potential. Here are some approximate salary ranges for common job roles related to CEH v12 certification:
Ethical Hacker/Penetration Tester: Entry-level professionals with CEH v12 certification may earn an annual salary of $60,000 to $90,000. As you gain experience, your salary can increase from $90,000 to $120,000 or more, depending on your skill set and the demands of the job market.
Security Analyst: Security analysts with CEH v12 certification can earn around $70,000 to $100,000 per year, with higher salaries possible for those with significant experience or specialized knowledge in areas such as threat intelligence or incident response.
Security Consultant: Security consultants with CEH v12 certification often work in consulting firms or as independent contractors. Their salaries can range from $80,000 to $130,000 or more, depending on their level of expertise, reputation, and the complexity of the projects they handle.
Security Engineer: Security engineers design and implement security solutions, manage security infrastructure, and perform vulnerability assessments. With a CEH v12 certification, their salaries typically range from $80,000 to $120,000 per year, depending on experience and job location.
Security Manager: Security managers are responsible for overseeing the organization’s cybersecurity strategy, managing teams, and ensuring compliance with security standards. Salaries for security managers with CEH v12 certification can vary widely but often fall in the range of $100,000 to $150,000 or more, depending on the size and complexity of the organization.
It’s important to note that these figures are approximate and can vary significantly depending on various factors. Additionally, the job market and regional variations can impact salary ranges. To get a more accurate understanding of the salary range in your specific location and industry, it’s recommended to research job listings, consult salary surveys, and network with professionals in the field.
Summarize:
The CEH v12 certification is one of the most popular certifications in cybersecurity, with hard work and practice helping you pass the exam with ease!
Finally, I wish all candidates get the job they want and earn a high salary!