The latest EC-COUNCIL ECSAV10 dumps by Lead4Pass helps you pass the ECSAV10 exam for the first time! Lead4Pass
Latest Update EC-COUNCIL ECSAV10 VCE Dump and ECSAV10 PDF Dumps, Lead4Pass ECSAV10 Exam Questions Updated, Answers corrected!
Get the latest Lead4Pass ECSAV10 dumps with Vce and PDF: https://www.leads4pass.com/ecsav10.html (Q&As: 354 dumps)
[Free ECSAV10 PDF] Latest EC-COUNCIL ECSAV10 Dumps PDF collected by Lead4pass Google Drive:
https://drive.google.com/file/d/1fzMt_lM5IgmjOvlQ9E11V38na89gbN2j/
[Lead4pass ECSAV10 Youtube] EC-COUNCIL ECSAV10 Dumps can be viewed on Youtube shared by Lead4Pass
Latest EC-COUNCIL ECSAV10 Exam Practice Questions and Answers
QUESTION 1
A month ago, Jason, a software developer at a reputed IT firm was surfing through his company\\’s website. He was
visiting random pages of the company\\’s website and came to find confidential information about the company was
posted on
one of the web pages. Jason forgot to report the issue. Jason contacted John, another member of the Security Team,
and discussed the issue. John visited the page but found nothing wrong.
What should John do to see past versions and pages of a website that Jason saw one month back?
A. John should use SmartWhois to recover the old pages of the website
B. John should recover cashed pages of the website from the Google search engine cache
C. John should run the Web Data Extractor tool to recover the old data
D. John can go to Archive.org to see past versions of the company website
Correct Answer: D
QUESTION 2
Which of the following pen-testing reports provides detailed information about all the tasks performed during penetration
testing?
A. Client-Side Test Report
B. Activity Report
C. Host Report
D. Vulnerability Report
Correct Answer: A
QUESTION 3
John, the penetration testing manager in a pen testing firm, needs to prepare a pen testing pricing report for a client.
Which of the following factors does he need to consider while preparing the pen testing pricing report?
A. Number of employees in the client organization
B. Complete structure of the organization
C. Number of client computers to be tested and resources required to perform a pen test
D. Number of servers available in the client organization
Correct Answer: C
QUESTION 4
An attacker with a malicious intention decided to hack confidential data from the target organization. For acquiring such
information, he started testing IoT devices that are connected to the target network. He started monitoring the network
traffic passing between the IoT devices and the network to verify whether credentials are being transmitted in cleartext.
Further, he also tried to crack the passwords using well-known keywords across all the interfaces.
Which of the following IoT threats the attacker is trying to exploit?
A. Poor physical security
B. Poor authentication
C. Privacy concerns
D. Insecure firmware
Correct Answer: B
QUESTION 5
Jason is a penetration tester, and after completing the initial penetration test, he wanted to create a final penetration test
report that consists of all activities performed throughout the penetration testing process. Before creating the final
penetration testing report, which of the following reports should Jason prepare in order to verify if any crucial information
is missed from the report?
A. Activity report
B. Host report
C. User report
D. Draft report
Correct Answer: A
QUESTION 6
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides top-level guidance for conducting penetration testing. Various factors are considered while preparing the scope of ROE which clearly explains the limits associated with the security test.
Which of the following factors is NOT considered while preparing the scope of the Rules of Engagement (ROE)?
A. A list of employees in the client organization
B. A list of acceptable testing techniques
C. Specific IP addresses/ranges to be tested
D. Points of contact for the penetration testing team
Correct Answer: A
QUESTION 7
An organization recently faced a cyberattack where an attacker captured legitimate user credentials and gained access
to the critical information systems. He also led other malicious hackers in gaining access to the information systems. To
defend and prevent such attacks in the future, the organization has decided to route all the incoming and outgoing network
traffic through a centralized access proxy apart from validating user credentials.
Which of the following defensive mechanisms the organization is trying to strengthen?
A. Authentication
B. Serialization
C. Encryption
D. Hashing
Correct Answer: A
QUESTION 8
Which one of the following is a useful formatting token that takes an int * as an argument, and writes the number of
bytes already are written, to that location?
A. “%n”
B. “%s”
C. “%p”
D. “%w”
Correct Answer: A
QUESTION 9
What are placeholders (or markers) in an HTML document that the webserver will dynamically replace with data just
before sending the requested documents to a browser?
A. Server Side Includes
B. Sort Server Includes
C. Server Sort Includes
D. Slide Server Includes
Correct Answer: A
QUESTION 10
You are running through a series of tests on your network to check for any security vulnerabilities. After normal working
hours, you initiate a DoS attack against your external firewall. The firewall quickly freezes up and becomes unusable.
You then initiate an FTP connection from an external IP into your internal network. The connection is successful even
though you have FTP blocked at the external firewall. What has happened?
A. The firewall failed-open
B. The firewall failed-bypass
C. The firewall failed-closed
D. The firewall ACL has been purged
Correct Answer: A
QUESTION 11
Martin works as a professional Ethical Hacker and Penetration Tester. He is an ESCA certified professional and was
following the LPT methodology to perform penetration testing. He is assigned a project for information gathering on
a
client\\’s network. He started penetration testing and was trying to find out the company\\’s internal URLs, (mostly by trial
and error), looking for any information about the different departments and business units. Martin was unable to find
any
information.
What should Martin do to get the information he needs?
A. Martin should use email tracking tools such as eMailTrackerPro to find the company\\’s internal URLs
B. Martin should use online services such as netcraft.com to find the company\\’s internal URLs
C. Martin should use WayBackMachine in Archive.org to find the company\\’s internal URLs
D. Martin should use website mirroring tools such as HTTrack Web Site Copier to find the company\\’s internal URLs
Correct Answer: D
QUESTION 12
Windows stores user passwords in the Security Accounts Manager database (SAM), or in the Active Directory database
in domains. Passwords are never stored in clear text; passwords are hashed and the results are stored in the SAM.
NTLM and LM authentication protocols are used to securely store a user\\’s password in the SAM database using
different hashing methods.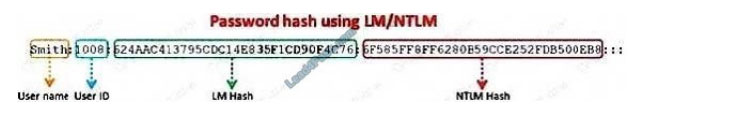
The SAM file in Windows Server 2008 is located in which of the following locations?
A. c:\windows\system32\config\SAM
B. c:\windows\system32\drivers\SAM
C. c:\windows\system32\Setup\SAM
D. c:\windows\system32\Boot\SAM
Correct Answer: D
QUESTION 13
Richard, a penetration tester was asked to assess a web application. During the assessment, he discovered a file
upload field where users can upload their profile pictures. While scanning the page for vulnerabilities, Richard found a
file
upload exploit on the website. Richard wants to test the web application by uploading a malicious PHP shell, but the
web page denied the file upload. Trying to get around the security, Richard added the `jpg\\’ extension to the end of the
file.
The new file name ended with `.php.jpg\\’. He then used the Burp suite tool and removed the `jpg\\’\\’ extension from the
request while uploading the file. This enabled him to successfully upload the PHP shell.
Which of the following techniques has Richard implemented to upload the PHP shell?
A. Session stealing
B. Cookie tampering
C. Cross-site scripting
D. Parameter tampering
Correct Answer: D
latest updated EC-COUNCIL ECSAV10 exam questions from the Lead4Pass ECSAV10 dumps! 100% pass the ECSAV10 exam!
Download Lead4Pass ECSAV10 VCE and PDF dumps: https://www.leads4pass.com/ecsav10.html (Q&As: 354 dumps)
Get free EC-COUNCIL ECSAV10 dumps PDF online: https://drive.google.com/file/d/1fzMt_lM5IgmjOvlQ9E11V38na89gbN2j/